In this demo, I will use Cloudformation StackSets to create an IAM group in all accounts.
When you have AWS organization, you can do mass changes with ease. In this example, I will be creating an IAM group in all accounts using Cloudformation StackSets.
Create a cloudformation template
First, create a cloudformation template in your computer, save this to a file. IAM group is a safe resource to test. It does not incur any fees, and an empty IAM group poses no security risk.
AWSTemplateFormatVersion: "2010-09-09"
Description: "IAM group creation stack set"
Resources:
IAMGroup:
Type: "AWS::IAM::Group"
Properties:
GroupName: "CfStackSetTest"
Outputs:
IAMGroupId:
Description: "The ID of the created IAM group"
Value: !Ref IAMGroupCreate a Cloudformation StackSet
Log into the master payer account, go to cloudformation stacksets > Create StackSet. In the next page, accept the defaults and upload the cloudformation template from your computer.
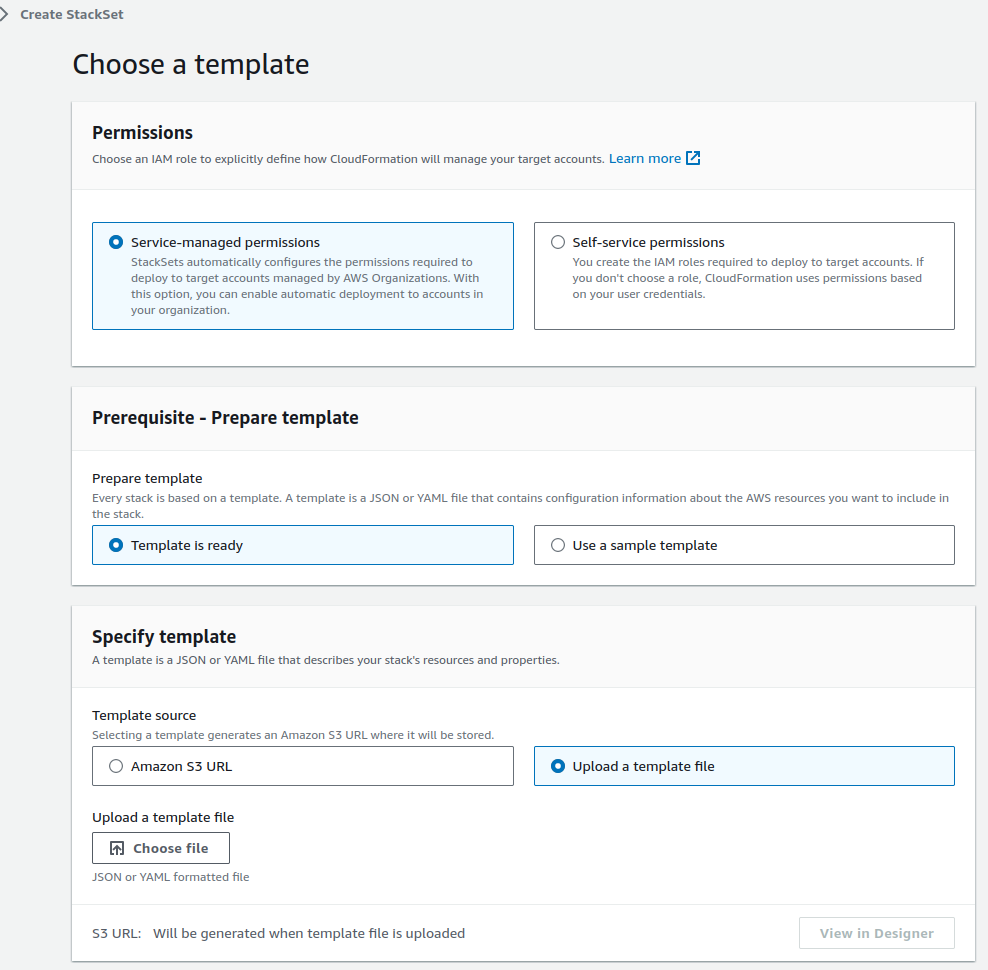
Next, fill in the stackset name and description.
Next, set the tags you wish to associate with this stackset. Under managed execution, I selected Active.
Next, you will be asked to provide additional settings. Choose Deploy new stacks and Deploy to organization. In the auto-deployment option, I choose Deactivated. I do not want cloudformation to automatically apply this stackset to new member accounts.
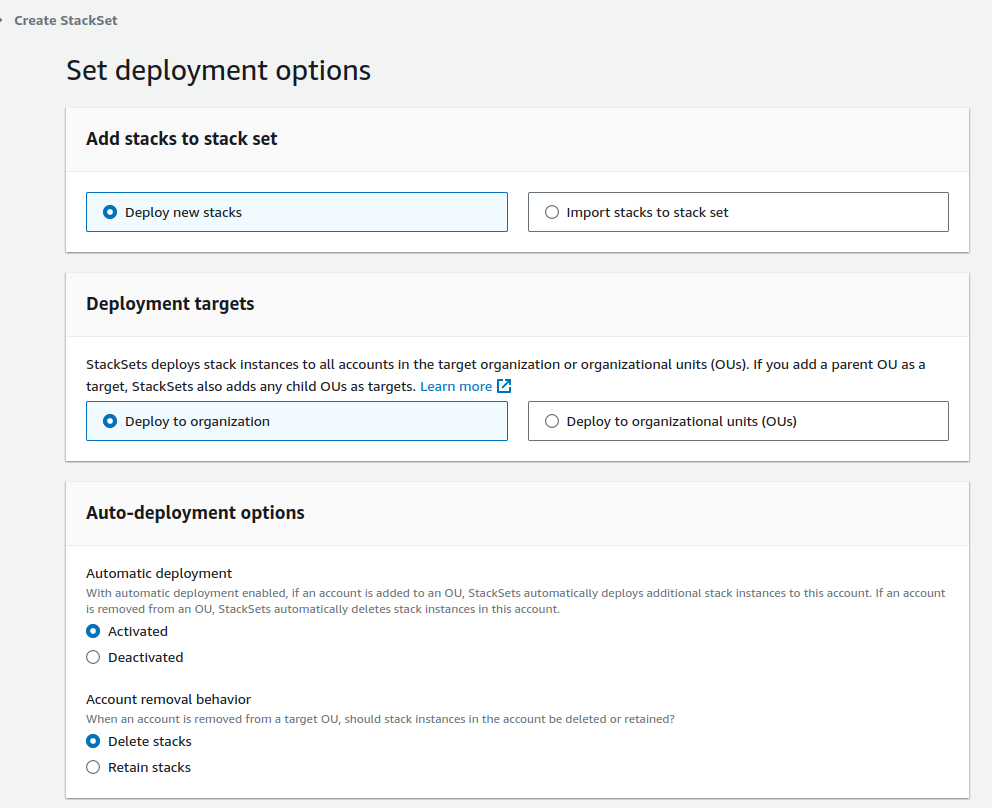
At the second half of the screen, provide the region and deployment options. Since I’m creating a IAM group only, I can use high concurrency.
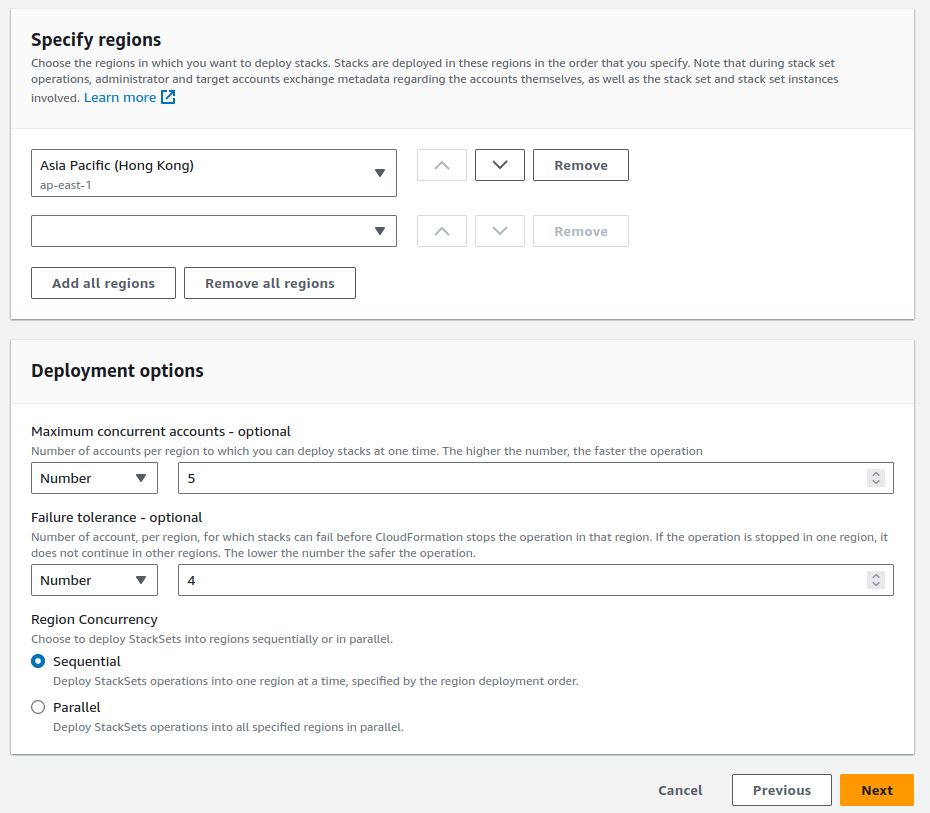
On the next screen, acknowledge the disclaimer and click submit.
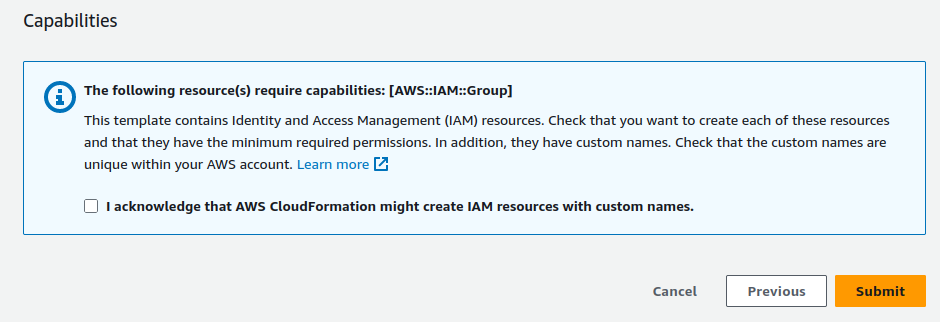
Give it 5-10 minutes and check the operations status for your stackset. When completed, the status will change to SUCCEEDED.
Undo changes
All great. Now, how do I go about deleting this IAM group? Go to the stackset, open the Stack instances tab, and then from the actions menu, choose Delete stacks from StackSet.
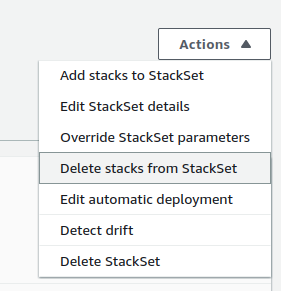
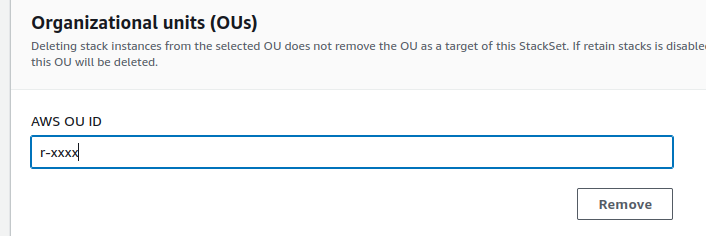
Next, enter the OU ID. In my case, I want to delete this stack from the root OU, which includes all member accounts.
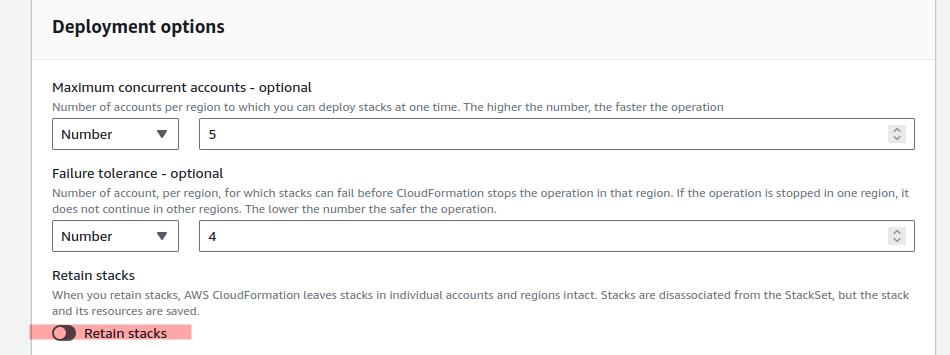
In the Deployment options section, enter the concurrency setting and ensure Retain stacks is unchecked. This tells cloudformation to delete the IAM group.
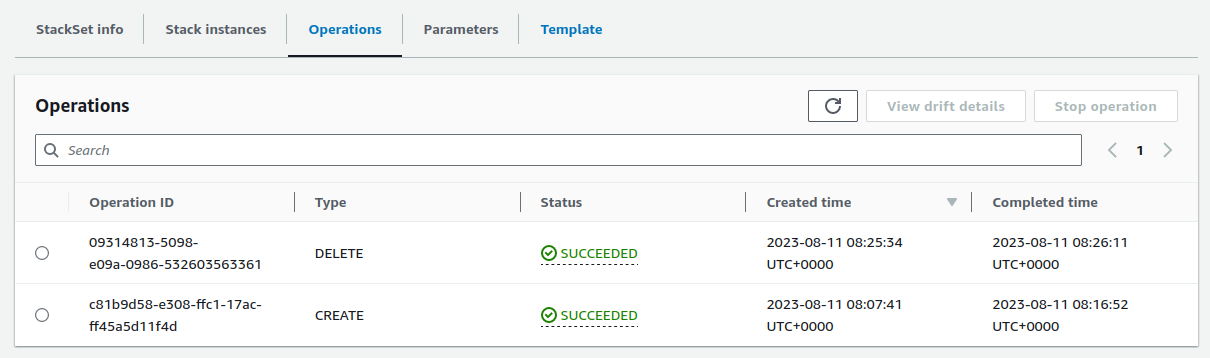
When completed, you will see the status turns to SUCCEEDED on the Operations tab.
Finally, delete the StackSet if it is no longer useful. Empty and delete the S3 bucket storing the cloudformation template. You will find it in the S3 console. The bucket name is cf-templates-xxxxx-<region>.
Final thoughts
This really simplifies administration especially when you have many member accounts. You don’t even need to worry about creating cross-account access. Cloudformation does that for you automatically.
![]()
